Last Updated: January 2026
Introduction: Size Doesn’t Equal Danger
You’ve heard the headlines: “3 billion accounts hacked.” “500 million records stolen.” These numbers are designed to shock you, but they don’t tell you what actually matters—how much danger are YOU in right now?
Here’s the truth most data breach lists won’t tell you: A leak of 1 billion old email addresses from 2013 is far less dangerous than a leak of 1 million Social Security Numbers from last week. A database of Yahoo passwords matters less than a database of your DNA.
This list is different. We didn’t rank these breaches by the size of the headlines. We ranked them by the Danger Score—a measurement of how much damage each breach can do to you today, in 2026.
Not Sure If You’re Affected?
Don’t want to scroll through 50 breaches? Check if your data is exposed right now
How We Ranked the “Danger Score”
Most lists just count the number of files hacked. We don’t.
A billion emails from 2012 matters less than 1,000 credit card numbers from yesterday. A leak of your Netflix password is annoying. A leak of your biometric data is permanent.
We graded every breach on a 1-10 scale based on three factors:
1. Permanence (Can You Change It?)
- Passwords: You can reset them. Danger fades over time.
- Social Security Numbers: You cannot change these. The danger is permanent.
- DNA/Biometric Data: Impossible to change. Once leaked, forever leaked.
2. Weaponization (Is It Being Used Right Now?)
- Is this data currently being traded on dark web forums?
- Are scammers actively using it for identity theft, SIM swaps, or credential stuffing?
- Some breaches from 2015 are more dangerous today than they were when they happened.
3. The Silo Effect (Does It Unlock Other Accounts?)
- Email breaches are “master keys”—they unlock password resets for banks, social media, and everything else.
- Phone number leaks enable SIM swapping and 2FA bypass.
- Single-site leaks (like a gaming platform) have limited blast radius.
This methodology is why some smaller breaches rank higher than billion-record leaks. A 100 million record leak of SSNs is more dangerous than a 3 billion record leak of old passwords.
Jump to a Section
Fast Navigation:
- The Billion Club (Catastrophic Scale)
- Big Tech & Social Media (The Trust Breakers)
- The Life Ruiners (Biometric & Financial)
- The Recent Wave (2024-2025)
- The Complete Ranked Table (21-50)
- What to Do Next
The “Billion Club” (The Catastrophic Tier)
These are the giants—breaches so massive they affected more than 1 billion records. But remember: scale doesn’t automatically mean danger. Some of these leaks involved old, low-value data. Others exposed information that will haunt victims for decades.
1. Yahoo (2013-2014) – 3 Billion Accounts
The Largest Confirmed Breach in History
What Was Stolen
- Real names
- Email addresses
- Dates of birth
- Telephone numbers
- Hashed passwords (using outdated MD5 encryption)
- Security questions and answers
The Reality Check
Every single Yahoo user—essentially the entire platform—was compromised. The breach wasn’t discovered until 2016, meaning attackers had years to weaponize this data. By the time Yahoo admitted the full scale in 2017, the damage was done.
Why It Still Matters in 2026
If you had a Yahoo account in 2013, attackers know your mother’s maiden name, your first pet, and the answers to every “forgot password” question you’ve used since. Credential stuffing remains one of the most common attack methods in breach incident reports—people reuse these old passwords and security answers across Netflix, Amazon, and banking apps.
Danger Score: 4/10
Reasoning: The data is old and most passwords have been changed. However, the security question answers are permanent and still exploited in social engineering attacks.
2. National Public Data (2024) – 2.9 Billion Records
The Background Check Catastrophe
What Was Stolen
- Full names
- Physical addresses (current and historical)
- Social Security Numbers
- Phone numbers
- Data spanning Americans, Canadians, and UK citizens
The Reality Check
National Public Data is a background check company that scraped and aggregated public records. They left a database containing nearly every American’s SSN exposed without password protection. This wasn’t a hack—it was negligence.
Why This Is a 10/10 Disaster
Your Social Security Number cannot be changed. If it’s in this leak (and statistically, it likely is), scammers can:
- File fraudulent tax returns in your name
- Open credit cards you’ll never know about until collections calls start
- Take out loans against your identity
- Access your medical records
This is the breach that makes credit freezes non-negotiable.
Danger Score: 10/10
Reasoning: Permanent, unchangeable identity data that is actively being used for fraud right now.
What You Must Do: If you haven’t frozen your credit yet, this is why you need to. Learn how to lock down your identity
3. Real Estate Wealth Network (2023) – 1.5 Billion Records
The Celebrity Address Database
What Was Stolen
- Property ownership data
- Home addresses (including celebrity and high-net-worth individuals)
- Mortgage details
- Property valuations
The Reality Check
This database was left completely exposed—no password, no authentication, nothing. It contained detailed property records including the home addresses of celebrities, politicians, and executives.
Why It Matters
For most people, this enables targeted burglary and For public figures, it’s a stalking and security nightmare. For real estate investors, it exposed their entire portfolios to competitors.
Danger Score: 6/10
Reasoning: High sensitivity for specific victims (public figures, wealthy individuals), moderate risk for average homeowners. Property data is semi-public anyway, but aggregation makes targeting easier.
4. River City Media (2017) – 1.37 Billion Records
The Spam Empire Collapse
What Was Stolen
- Email addresses (1.37 billion unique addresses)
- Names
- IP addresses
- Physical addresses
The Reality Check
River City Media was a spam operation that sent billions of unsolicited emails. When their backup server was left exposed, researchers discovered the entire database—effectively a map of every email address that had ever been scraped from the internet.
Why It Still Matters
This database is the backbone of modern spam and phishing operations. If your email was active before 2017, it’s in this list. This is why your inbox is a warzone.
Danger Score: 5/10
Reasoning: Email addresses alone aren’t immediately dangerous, but they’re the starting point for phishing, social engineering, and credential stuffing. The scale makes this a permanent problem.
5. Aadhaar (India, 2018) – 1.1 Billion Records
The Biometric National ID Breach
What Was Stolen
- Aadhaar ID numbers (India’s national ID system)
- Names
- Biometric data (fingerprints, iris scans)
- Connected bank account details
- Phone numbers
The Reality Check
Aadhaar is India’s mandatory biometric ID system—essentially the Social Security Number on steroids. Multiple investigations and security researchers documented widespread unauthorized access through insecure government portals that were selling access for as little as 500 rupees ($6 USD). The breach exposed the identity data of nearly every Indian citizen.
Why This Is Catastrophic for Indian Citizens
Aadhaar is required for:
- Opening bank accounts
- Filing taxes
- Receiving government benefits
- SIM card registration
You cannot opt out. You cannot change your biometric data. Once leaked, your identity is compromised forever.
For over a billion people, this wasn’t a privacy failure—it was a life sentence.
Danger Score: 10/10
Reasoning: Biometric data is permanent and unchangeable. This breach affects 1.1 billion people who have no recourse.
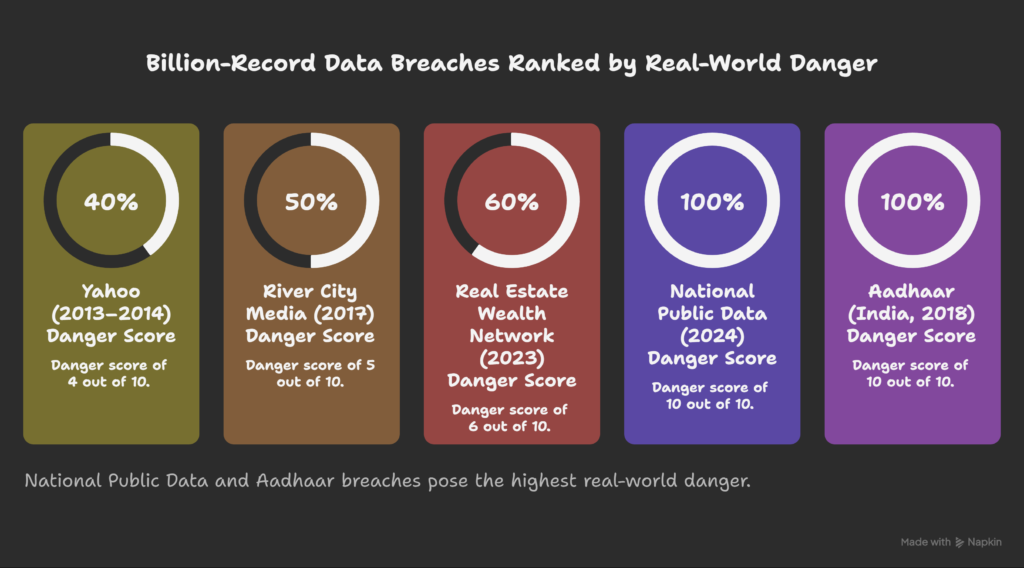
Pattern to Notice: Every breach in the Billion Club involved either permanent data (SSNs, biometrics) or data that unlocks other accounts. Size alone didn’t cause the damage—what was stolen did.
Big Tech & Social Media (The Trust Breakers)
The Billion Club showed us scale. Now, let’s examine something more personal: betrayal by the platforms you use every day.
These companies promised to protect your data. They built billion-dollar empires on that promise. Then, they failed—sometimes through negligence, sometimes through deliberate exploitation, and often through third-party vendors they never properly vetted.
What makes these breaches particularly dangerous isn’t just the data stolen—it’s the trust destroyed. When Facebook leaks your phone number, scammers don’t just spam you. They impersonate Facebook itself, knowing you’re more likely to trust a message that appears to come from a platform you already use daily.
6. Meta/Facebook (2019/2021) – 533 Million Users
The Breach That Powers Today’s Spam Industry
What Was Stolen
Scrapers collected and leaked:
- Phone numbers
- Full names
- Facebook IDs
- Locations (cities/countries)
- Birthdates
- Email addresses
- Relationship status
- Employer information
The Reality Check
This wasn’t a traditional “hack.” Instead, attackers exploited Facebook’s contact importer feature, which allowed them to scrape massive amounts of user data before Facebook patched the vulnerability. By the time Facebook discovered the abuse in 2019, attackers had already extracted data from 533 million accounts across 106 countries.
Then, in 2021, someone posted the entire database for free on hacking forums.
Consequently, this data became instantly accessible to every scammer, phisher, and identity thief on the planet.
Why This Breach Still Matters
Here’s what’s happening right now with your leaked Facebook data:
SMS Phishing (Smishing): Scammers text you using your real name and city, making their messages seem legitimate. For instance: “Hi Sarah from Chicago, your package is waiting. Click here…”
Caller ID Spoofing: They call you pretending to be Facebook support, already knowing your account details before you even answer.
SIM Swapping: Armed with your phone number, birthdate, and location, attackers convince mobile carriers they’re you, then hijack your number to bypass two-factor authentication.
Targeted Social Engineering: They know who you work for and where you live, making their phishing emails disturbingly specific.
Danger Score: 8/10
Reasoning: Phone numbers serve as master keys to modern identity. Moreover, this data actively fuels the spam and scam industry today—not in 2019, but right now in 2026.
🛑 Deep Dive Analysis: This leak proved Facebook cannot protect you. We analyzed exactly how attackers use this data for SMS phishing in 2026. 👉 Read: The Facebook 533M Leak: Why It Still Matters Today
7. Google+ API Exposure (2018) – 52.5 Million Users
The Social Network Google Killed to Hide the Truth
What Was Stolen
A software glitch exposed:
- Names
- Email addresses
- Occupation details
- Dates of birth
- Profile photos
- Private profile information marked “not public”
The Reality Check
Google discovered a bug in the Google+ API that allowed app developers to access private user data—information users had explicitly marked as private. Even more concerning, Google found this vulnerability in March 2018 but didn’t disclose it publicly until October 2018.
Why the delay?
Internal documents later revealed that Google executives worried about regulatory scrutiny and compared the situation to Facebook’s Cambridge Analytica scandal. Ultimately, Google chose to shut down the entire Google+ social network rather than face the public relations nightmare.
Why This Breach Still Matters
Unlike Facebook, which primarily operates one platform, Google controls your entire digital ecosystem:
- Gmail (your email)
- Google Drive (your documents)
- Google Photos (your memories)
- Google Calendar (your schedule)
- Android (your phone’s operating system)
- Chrome (your browsing history)
Therefore, when Google suffers an API vulnerability, attackers potentially gain access to everything. This is what security experts call the “Content Silo” problem—putting all your eggs in one basket makes that basket a high-value target.
Danger Score: 5/10
Reasoning: The specific data leaked wasn’t catastrophic. However, the incident revealed systemic API security problems across Google’s infrastructure, and the company’s decision to hide the breach for seven months eroded user trust significantly.
🛑 Deep Dive Analysis: Google’s ecosystem creates a “Content Silo” of your entire life. Discover how their API vulnerabilities put you at risk across multiple services. 👉 Read: Google’s Hidden Data Leaks: A History of Silence
8. LinkedIn (2021) – 700 Million Users
92% of the Entire User Base Scraped and Sold
What Was Stolen
Attackers scraped and posted for sale:
- Full names
- Email addresses
- Phone numbers
- Workplace information
- Geographic locations
- LinkedIn profile URLs
- Professional experience
- Other public profile data
The Reality Check
In April 2021, a hacker put 700 million LinkedIn user records up for sale on a dark web forum—representing 92% of LinkedIn’s total user base at the time.
Although LinkedIn claimed this was merely “data scraping” rather than a breach, that distinction matters little to the victims whose information was bundled and sold.
Furthermore, this marked LinkedIn’s second major exposure. Previously, in 2012, hackers stole 165 million user emails and passwords, which later surfaced on the dark web in 2016.
Why This Breach Still Matters
LinkedIn breaches enable a specific type of attack that consumer platforms cannot: business email compromise (BEC).
Scammers leverage your leaked LinkedIn data to:
Impersonate Executives: They email your finance team pretending to be the CFO, using real names and titles from LinkedIn to add legitimacy.
Target Specific Employees: They identify who handles payments, who has system access, and who reports to whom—then craft personalized phishing emails accordingly.
Clone Your Network: They create fake LinkedIn profiles using your colleagues’ stolen information, then connect with you to deliver malware or extract confidential information.
Research Your Vulnerabilities: They study your job history, skills, and connections to design social engineering attacks tailored specifically to you.
Danger Score: 7/10
Reasoning: While the data itself consists of publicly available information, its aggregation and sale enable sophisticated corporate espionage and business email compromise attacks. Additionally, the sheer scale (92% of users) makes evasion nearly impossible.
9. Twitter/X (2022) – 220 Million Users
The Email-to-Handle Database
What Was Stolen
Attackers scraped and leaked:
- Email addresses
- Twitter handles (usernames)
- Account creation dates
- Follower counts
- Following counts
The Reality Check
In 2022, hackers exploited an API vulnerability that allowed them to input email addresses and receive the associated Twitter handles in return. They systematically scraped 220 million user records, then sold the database on dark web forums.
What makes this breach particularly insidious is the connection it creates.
Previously, if you used a pseudonymous Twitter account to protect your privacy, your email address remained hidden. Now, anyone who knows your email can potentially discover your “anonymous” Twitter identity.
Why This Breach Still Matters
This breach specifically endangers:
Whistleblowers: Journalists and activists who used anonymous accounts to expose corruption can now be identified through their email addresses.
Abuse Survivors: People who escaped domestic violence and created new online identities under pseudonyms can be tracked by their abusers.
Private Individuals: Anyone who wanted to separate their professional email from their personal Twitter opinions lost that separation permanently.
Businesses: Corporate email addresses now link to employees’ personal Twitter accounts, exposing unprofessional tweets or controversial opinions.
Additionally, in 2018, Twitter suffered another breach when a glitch stored passwords in plaintext on internal logs, exposing 330 million user passwords to potential insider threats.
Danger Score: 6/10
Reasoning: The data doesn’t include passwords or financial information. Nevertheless, it permanently destroys pseudonymous privacy and enables targeted harassment campaigns. Moreover, the email-username connection facilitates credential stuffing attacks across other platforms.
10. Instagram (2020) – 200 Million Users
The Third-Party Partner Catastrophe
What Was Stolen
A partner company (Socialarks) exposed a database containing:
- Instagram usernames
- Full names
- Phone numbers
- Email addresses
- Profile photos
- Follower counts
- Biographical information
The Reality Check
Instagram didn’t get hacked directly. Instead, Socialarks—a social media marketing company that Instagram users connected to their accounts—left an unsecured database containing 200 million Instagram user records accessible online without password protection.
This illustrates a critical vulnerability in the modern app ecosystem: you’re only as secure as the weakest third-party app you’ve ever authorized.
Why This Breach Still Matters
Every time you click “Continue with Facebook” or “Authorize Instagram Access,” you’re handing your data to another company with potentially weaker security standards.
Subsequently, you often forget these authorizations exist—yet they persist indefinitely unless you manually revoke them.
Consider this: Even if Instagram (owned by Meta) maintains perfect security, any of the dozens of third-party apps you’ve connected over the years could expose your data. Moreover, many users cannot even remember which apps they’ve authorized, making it impossible to assess their current exposure.
Danger Score: 7/10
Reasoning: Phone numbers and email addresses fuel phishing campaigns and account takeover attempts. Furthermore, this breach highlights a systemic problem: third-party app vulnerabilities that users cannot control even with strong personal security practices.

Pro Tip: Immediately review and revoke third-party app access on all your social media accounts. On Instagram: Settings → Security → Apps and Websites. Most users discover dozens of forgotten authorizations.
The “Life Ruiners” (Biometric & Financial Data)
The Billion Club showed us scale. Big Tech showed us betrayal. Now, let’s examine something far worse: permanent damage.
These breaches exposed data you cannot change. You can reset your password, you can get a new email address and You can even change your phone number.
But you cannot change your Social Security Number. You cannot change your DNA. You cannot rewrite your credit history.
When this type of data leaks, the consequences follow you for life. These are the breaches that transform victims into permanent targets, forcing them to live in a state of defensive vigilance forever.
11. Equifax (2017) – 147 Million People
The Death of Financial Privacy
What Was Stolen
Hackers compromised:
- Full names
- Social Security Numbers
- Birth dates
- Physical addresses
- Driver’s license numbers
- Credit card numbers (209,000 people)
The Reality Check
Equifax is one of the three major credit bureaus that determine your financial trustworthiness in America. In 2017, hackers exploited a known vulnerability that Equifax failed to patch for months. They maintained access to Equifax’s systems for 76 days before detection.
Here’s the devastating part: You never chose to give Equifax your data.
You never signed up for their service. You never agreed to their terms. Nevertheless, they collected your entire financial history without your consent, then failed to protect it.
Why This Breach Still Matters
Your Social Security Number serves as the master key to your financial identity in the United States. With it, criminals can:
File Fraudulent Tax Returns: They file fake returns in your name, claim your refund, and disappear. Meanwhile, the IRS rejects your legitimate return and demands you prove your identity.
Open Credit Accounts: They apply for credit cards, auto loans, and mortgages using your SSN. You won’t discover these accounts until debt collectors start calling.
Access Medical Care: They use your identity to receive medical treatment, creating false medical records that could affect your insurance coverage and even endanger your life if doctors reference the wrong medical history.
Claim Government Benefits: They collect unemployment, Social Security, or disability benefits in your name, creating tax liabilities you’ll have to dispute for years.
Moreover, SSN changes are nearly impossible to obtain. The Social Security Administration only issues new numbers in extreme circumstances, and even then, your old number remains linked to your credit history forever.
Danger Score: 10/10
Reasoning: Social Security Numbers are permanent financial identifiers. This breach created 147 million permanent victims who must monitor their credit for life. The data will remain valuable to criminals for decades.
🛑 Deep Dive Analysis: You cannot change your Social Security Number. Here is how to live in a post-Equifax world with permanent defensive strategies. 👉 Read: The Equifax Aftermath: Your Forever Defense Strategy
12. 23andMe (2023) – 6.9 Million Users
The DNA Database That Targeted Ethnicities
What Was Stolen
Attackers accessed and scraped:
- DNA ancestry composition
- Family trees and relative matches
- Health predisposition reports
- Geographic ancestry data
- Ethnic heritage percentages
- Usernames and profile photos
The Reality Check
In October 2023, hackers used credential stuffing attacks (passwords stolen from other breaches) to access 23andMe accounts. However, they didn’t just steal the data of compromised accounts.
They exploited 23andMe’s “DNA Relatives” feature.
This feature allows users to see relatives who also use 23andMe. Consequently, by accessing one account, attackers could scrape data from that person’s entire family tree—even relatives who had strong passwords and two-factor authentication enabled.
The attackers specifically targeted and compiled profiles of Ashkenazi Jewish users and Chinese users, selling these datasets separately on dark web forums.
Why This Breach Still Matters
Unlike every other type of data, your DNA cannot be changed. Ever. This creates several unprecedented dangers:
Genetic Discrimination: Insurance companies or employers could theoretically use leaked genetic data to deny coverage or employment based on health predispositions, despite laws prohibiting this practice.
Targeted Biological Attacks: While currently theoretical, genetic data could enable future biological weapons designed to target specific ethnic groups or genetic profiles.
Family Privacy Violation: Even if you never used 23andMe, your genetic relatives’ data reveals information about your own DNA. You cannot opt out of your biology.
Permanent Surveillance: Genetic data enables identification forever. Even if you change your name, appearance, and location, your DNA remains constant and identifiable.
Furthermore, the fact that attackers specifically compiled ethnic profiles reveals something chilling: this wasn’t opportunistic theft. This was targeted genetic surveillance of specific populations.
For over 6.9 million people, this wasn’t a privacy failure—it was biological exposure with no expiration date.
Danger Score: 9/10
Reasoning: Genetic data is permanent, immutable, and reveals information about your relatives without their consent. The targeted ethnic profiling adds an additional layer of danger that transcends typical privacy concerns.
13. Marriott/Starwood Hotels (2018) – 500 Million Guests
Four Years of Undetected Surveillance
What Was Stolen
Attackers accessed:
- Full names and mailing addresses
- Phone numbers and email addresses
- Passport numbers (for international travelers)
- Starwood Preferred Guest account information
- Travel dates and reservations
- Payment card numbers and expiration dates (encrypted, but potentially decryptable)
The Reality Check
This wasn’t a quick smash-and-grab. Hackers maintained access to Starwood Hotels’ reservation system from 2014 until 2018—four full years of undetected surveillance.
When Marriott acquired Starwood in 2016, they inherited the breach without knowing it.
The attackers didn’t just steal a snapshot of data. They monitored every reservation, every check-in, every guest who stayed at a Starwood property worldwide for four years.
Why This Breach Still Matters
Passport numbers don’t expire when stolen. They remain valid for 10 years, giving criminals a massive window to exploit them:
Identity Forgery: Criminals create fake passports using your legitimate passport number, enabling international travel under your identity.
Border Crossing Fraud: Your passport number could be flagged at border crossings due to crimes committed by someone using your stolen credentials.
Financial Fraud Across Borders: Many international financial transactions require passport verification. Criminals use stolen passport data to open offshore accounts or conduct wire fraud.
Travel Pattern Intelligence: Nation-state actors used this breach to map the travel patterns of government officials, corporate executives, and high-value targets. They now know where these individuals travel, when, and with whom.
Additionally, this breach revealed a systemic vulnerability: corporate acquisitions often overlook cybersecurity due diligence. Marriott bought Starwood without discovering the four-year-old breach already in progress.
Danger Score: 8/10
Reasoning: Passport numbers are difficult to change and enable international identity fraud. The four-year surveillance period means attackers gained unprecedented intelligence on travel patterns and behavior. The breach affects international travelers indefinitely.
14. Capital One (2019) – 100 Million Applications
The Cloud Security Catastrophe
What Was Stolen
A hacker accessed:
- Credit card applications (current and prospective customers)
- Bank account numbers
- Social Security Numbers
- Transaction data and credit scores
- Names, addresses, and phone numbers
- Credit limits and payment history
The Reality Check
In 2019, a former Amazon Web Services (AWS) engineer exploited a misconfigured firewall to access Capital One’s cloud storage. She didn’t need to hack through elaborate security measures.
Instead, she simply walked through an open door.
Capital One had configured their AWS firewall to allow broad access from the internet, essentially leaving sensitive financial data exposed to anyone who knew where to look. The hacker downloaded over 100 million credit card applications spanning from 2005 to 2019.
Why This Breach Still Matters
Credit card applications contain everything needed for complete financial identity theft:
Full Financial Profile: Applications include income, employment history, assets, and debts—a complete map of your financial life.
Social Security Numbers: Once again, the unchangeable master key that enables all other fraud.
Historical Data: This breach exposed applications from 2005 onward, meaning even if you closed your Capital One account years ago, your data was still stolen.
Cloud Security Precedent: This breach proved that cloud storage isn’t inherently secure. Misconfigurations can expose vast amounts of data instantly, and companies often lack visibility into their own cloud security posture.
Moreover, Capital One only discovered the breach because the hacker bragged about it on GitHub and Slack. Without her public boasting, the breach might have remained undetected indefinitely.
Danger Score: 9/10
Reasoning: Credit card applications combined with SSNs enable comprehensive financial fraud. The 14-year span of stolen data means victims from 2005 remain at risk today. The ease of exploitation reveals systemic cloud security vulnerabilities across the financial industry.
15. First American Financial (2019) – 885 Million Records
The Unlocked Real Estate Database
What Was Stolen
Exposed without any authentication:
- Bank account numbers and statements
- Wire transfer receipts
- Mortgage and tax records
- Driver’s license images
- Social Security Numbers
- Digitized signatures
The Reality Check
This wasn’t a breach in the traditional sense. First American Financial, a real estate title insurance company, simply left 885 million documents publicly accessible on their website.
No password required, No authentication and No security whatsoever.
For over a year, anyone who modified a URL in their browser could access decades of real estate transaction records. A security researcher discovered the exposure in December 2019, but evidence suggests the data had been accessible since 2014.
Why This Breach Still Matters
Real estate transactions generate uniquely comprehensive identity documentation:
Complete Financial Transparency: Mortgage records reveal your income, assets, debts, and net worth with perfect accuracy.
Digitized Signatures: Criminals can use scanned signatures to forge legal documents, authorize wire transfers, or commit notary fraud.
Bank Account Details: Wire transfer receipts include routing numbers and account numbers, enabling direct theft or ACH fraud.
Property Intelligence: Criminals know exactly which homes are owned by elderly individuals, recently deceased persons, or absentee owners—prime targets for real estate fraud.
Furthermore, First American Financial never notified victims. The company quietly fixed the configuration error and moved on, leaving 885 million people unaware that their complete financial histories had been exposed for years.
Danger Score: 9/10
Reasoning: The combination of SSNs, bank accounts, and digitized signatures enables comprehensive financial and real estate fraud. The multi-year exposure window means this data circulated freely before discovery. Victims likely remain unaware of their exposure.
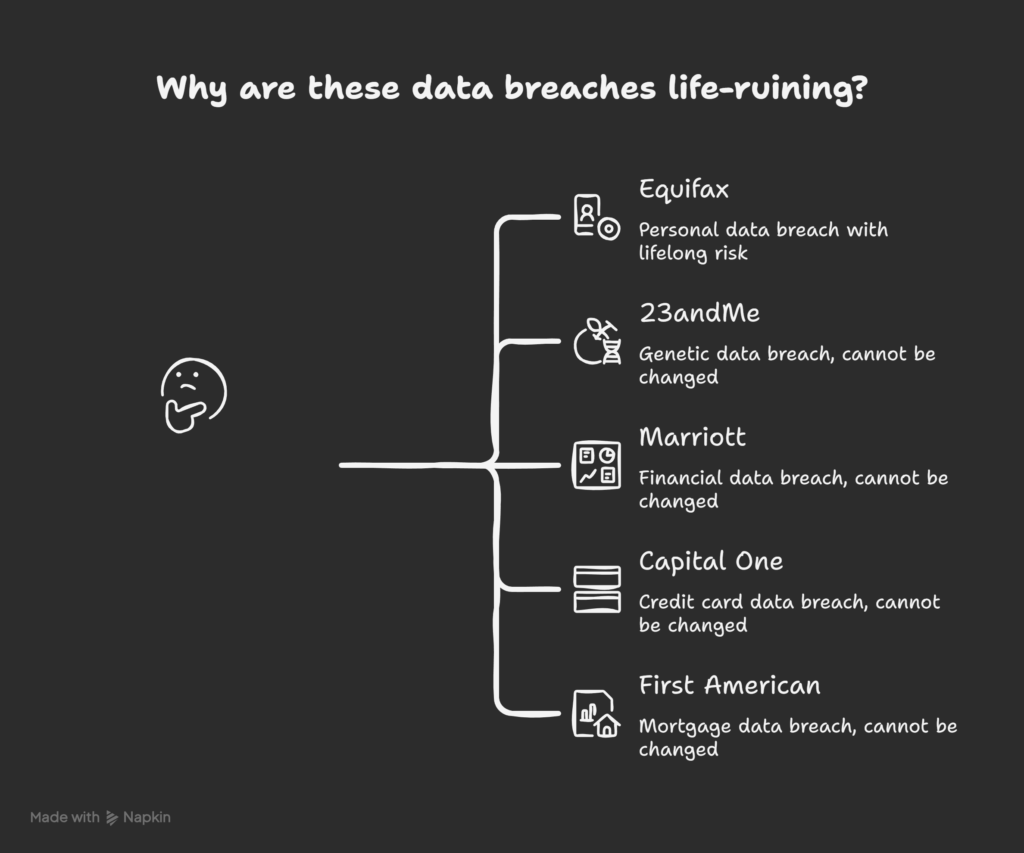
Pattern to Notice: Life-ruining breaches share one characteristic—they expose data that cannot be changed. Passwords can be reset. Email addresses can be abandoned. But Social Security Numbers, DNA, passport numbers, and digitized signatures follow you forever.
This is why a 100 million record breach of permanent data is more dangerous than a 1 billion record breach of disposable passwords.
The Recent Wave (2024-2025)
History matters. But urgency matters more.
The breaches above happened years ago. Their damage is done. Their data is already sold across criminal markets.
These breaches are different. They happened recently—some within the last few months.
If you’re affected by these leaks, criminals are using your data right now. Today. While you read this.
The investigations are still ongoing. The lawsuits are still being filed. The damage is still unfolding.
This section proves something critical: data breaches aren’t slowing down. They’re getting worse.
16. AT&T (2024) – 73 Million Users
Passcodes and SSNs on the Dark Web
What Was Stolen
Leaked data includes:
- Full names and addresses
- Email addresses and birth dates
- Phone numbers
- Social Security Numbers
- Account passcodes and PINs
The Reality Check
In March 2024, a huge dataset appeared on the dark web. It contained 73 million AT&T customer records.
At first, AT&T claimed the data was old. They said it might not even be from their systems.
Then, after weeks of investigation, they quietly confirmed it was real.
The breach likely happened years earlier. But the data only went public in 2024. This delay meant millions of AT&T customers were at risk for years. And they had no idea.
Why This Breach Still Matters
AT&T customers face immediate threats:
SIM Swap Attacks: Criminals have your passcode and PIN. They call AT&T pretending to be you. They ask for a SIM swap. This transfers your phone number to their device. Now they get all your text messages. This includes two-factor codes for your bank, email, and crypto accounts.
Account Takeover: Once they control your phone number, they lock you out. They do this to every account that uses SMS for password resets.
Social Security Number Fraud: Your SSN enables tax fraud. It lets criminals open credit accounts. It enables identity theft that lasts for years.
Targeted Phishing: Criminals use your real name, address, and phone number. They craft convincing phishing calls. They reference specific details about your AT&T account.
AT&T’s initial denial shows a common pattern. Companies delay. They deny. Then they quietly admit the truth after public pressure.
Danger Score: 9/10
Reasoning: Account passcodes plus SSNs enable immediate SIM swapping. They also enable long-term identity fraud. The breach is recent. Criminals are actively using this data now. The delayed disclosure gave attackers years of access.
🛑 Deep Dive Analysis: SIM swapping has become extremely dangerous. Learn how to protect your mobile number. 👉 Read: The AT&T Breach: How to Secure Your SIM Card Now
17. Ticketmaster (2024) – 560 Million Users
The Cloud Storage Crisis
What Was Stolen
The hacking group “ShinyHunters” stole:
- Full names and addresses
- Email addresses and phone numbers
- Partial payment card data
- Ticket purchase history
- Order details
The Reality Check
In May 2024, ShinyHunters announced they breached Ticketmaster. They accessed Ticketmaster’s cloud storage on Snowflake. That’s a popular data storage platform.
They put 560 million user records up for sale. The price? $500,000.
But this wasn’t just a Ticketmaster problem.
ShinyHunters hit multiple companies at the same time. All of them used Snowflake. The victims included Santander Bank and Advance Auto Parts.
The common problem? Many companies didn’t turn on multi-factor authentication. Their Snowflake accounts were protected by passwords alone.
Why This Breach Still Matters
This breach reveals a bigger problem:
Cloud Dependency Risk: Companies now store all their data in cloud platforms. These include Snowflake, AWS, and Azure. When these get breached, attackers gain access to everything at once.
Third-Party Trust Failures: Ticketmaster didn’t directly fail. Their cloud provider’s security did. But customers suffer either way.
Payment Card Exposure: Even “partial” payment data enables fraud. Criminals combine partial card numbers with other stolen data. Then they make fraudulent purchases.
Event Surveillance: Your ticket history reveals where you’ve been. It shows when you went and who you were with. For high-profile people, this enables stalking or targeted attacks.
The fact that multiple major companies fell victim suggests something worse. Many more companies using Snowflake may have been breached. They just haven’t disclosed it yet.
Danger Score: 7/10
Reasoning: The breach is very recent. It affects a massive number of users. Payment card data enables fraud. Event history reveals your behavior patterns. Multiple companies were hit at once. This suggests more victims will emerge. However, payment data was only partial. This limits immediate financial damage.
18. National Public Data (2024) – 2.9 Billion Records
[Covered in The Billion Club – See Entry #2]
Note: This breach happened in 2024. But its scale earned it a spot in The Billion Club section above. If you haven’t read about this SSN disaster yet, scroll up to Entry #2.
19. Dell (2024) – 49 Million Records
Customer Service Portal Exploit
What Was Stolen
Hackers scraped from Dell’s partner portal:
- Customer names
- Physical addresses
- Dell hardware service tags
- Order numbers and purchase dates
- Warranty information
The Reality Check
In May 2024, a hacker claimed to have scraped 49 million customer records. They got them from a Dell partner portal.
Dell downplayed the incident. They said no financial data was stolen. No payment information was accessed.
But they missed the point entirely.
Why This Breach Still Matters
Service tags and hardware IDs enable targeted attacks:
Fake Tech Support Scams: Criminals call you. They claim to be from Dell support and mention your exact computer model. They reference your service tag and purchase date. This is information only Dell “should” know. This makes their scam incredibly convincing.
Warranty Fraud: Attackers use your service tag to claim warranty repairs. They get replacements. Then they resell the hardware. Or they use it to access corporate networks.
Supply Chain Targeting: Corporate IT departments can be mapped through Dell purchases. Hackers see which companies use which hardware. Then they design attacks specifically for those systems.
Physical Address Exposure: Criminals know where expensive Dell equipment was shipped. This enables targeted burglary or theft.
The data came from a “partner portal.” This reveals a common problem. Companies secure their main systems. But they leave partner portals weakly protected.
Danger Score: 6/10
Reasoning: No financial data was exposed. But service tags enable convincing tech support scams. They enable warranty fraud. Corporate victims face supply chain risks. The breach is very recent. Exploitation is ongoing.
20. Change Healthcare (2024) – 100+ Million People
The Healthcare Ransomware Attack
What Was Stolen
A ransomware attack compromised:
- Medical records and diagnoses
- Prescription information
- Insurance details and claims
- Social Security Numbers
- Payment and billing information
- Protected health data spanning decades
The Reality Check
In February 2024, hackers attacked Change Healthcare. It’s one of the largest healthcare payment processors in America.
The attack didn’t just steal data. It crippled the entire healthcare payment system.
For weeks, hospitals couldn’t submit insurance claims. Pharmacies couldn’t verify prescriptions. Patients couldn’t fill medications.
Change Healthcare paid the hackers $22 million in bitcoin. They did this to restore operations.
But paying ransoms doesn’t guarantee data deletion. Evidence suggests the stolen data was not destroyed.
Why This Breach Still Matters
Medical records are uniquely dangerous:
Lifetime Exposure: Credit cards expire. Medical records don’t. A diagnosis from 2010 stays in your history forever.
Insurance Fraud: Criminals use stolen insurance info to submit fake claims. They get expensive treatments in your name. They resell prescription medications.
Medical Identity Theft: Someone else’s medical history gets mixed with yours. Emergency doctors might see the wrong blood type. They might miss allergies. They might reference wrong medications. These errors can be fatal.
Blackmail Potential: Sensitive medical conditions become leverage. Mental health records. Substance abuse history. Sexual health information. All of it can be used for extortion.
SSN and Financial Exposure: Healthcare records include Social Security Numbers. They include payment information. This enables all the usual identity theft.
Change Healthcare’s role as critical infrastructure means something worse. This single breach impacted virtually everyone who used the US healthcare system.
Danger Score: 10/10
Reasoning: Medical records are permanent. They’re irreplaceable. They’re deeply personal. The breach affects over 100 million people. It includes SSNs. The ransomware payment suggests data was copied. It likely still exists on criminal servers. Medical identity theft creates lifetime problems.
Pattern to Notice: Recent breaches target critical infrastructure. They hit telecom systems. They hit healthcare. They hit cloud services. Criminals target identity documents. SSNs. Medical records. Account PINs. They’ve shifted from stealing credit cards to stealing the foundations of identity itself. This is a major escalation in cyber warfare against ordinary people.
The Complete Ranked List (Breaches #21-50)
The breaches above earned detailed analysis. They represent the most dangerous, most recent, or most impactful attacks in history.
These remaining 30 breaches still matter. But their stories are shorter. Their impacts are more specific. Their data is older or less immediately dangerous.
We’ve ranked them by their Danger Score. We’ve explained why each one still matters today. This isn’t filler content—it’s essential context for understanding the full landscape of data breaches.
21. Alibaba (2019) – 1.1 Billion Records
Danger Score: 4/10
What Was Stolen
A developer scraped customer data over eight months:
- Usernames
- Mobile phone numbers
- Purchase history
Why It Still Matters
Phone numbers enable SMS phishing in China and beyond. Purchase history reveals spending patterns criminals use for targeted scams. The eight-month scraping window shows how long internal threats can go undetected.
22. MySpace (2016) – 360 Million Accounts
Danger Score: 3/10
What Was Stolen
Data from an old breach was released:
- Usernames
- Email addresses
- Passwords (weakly hashed)
Why It Still Matters
Password reuse remains the #1 security vulnerability. People who used their 2008 MySpace password still use it for their 2026 Netflix account. Credential stuffing attacks rely on these old databases.
23. Twitter Password Bug (2018) – 330 Million Users
Danger Score: 5/10
What Was Stolen
A software glitch stored passwords in plaintext:
- Unencrypted passwords
- Account credentials
Why It Still Matters
The bug exposed passwords to Twitter employees and internal systems. While Twitter claims no external breach occurred, insider threats remain a constant risk. Any employee with access could have copied this data.
24. Sina Weibo (2020) – 538 Million Users
Danger Score: 6/10
What Was Stolen
China’s largest social platform leaked:
- Real names
- Site usernames
- Gender information
- Location data
- Phone numbers
Why It Still Matters
For Chinese citizens, Weibo is mandatory for public discourse. The leaked phone numbers enable government surveillance and targeted harassment. Opposition voices can be identified and silenced.
25. Adult Friend Finder (2016) – 412 Million Accounts
Danger Score: 7/10
What Was Stolen
The adult network exposed:
- Names and email addresses
- Passwords (some in plaintext)
- Sexual preferences
- Private messages
Why It Still Matters
Extortion and blackmail. Criminals target married users or public figures with threats to expose their activity. The sensitive nature makes victims more likely to pay ransom demands.
26. eBay (2014) – 145 Million Users
Danger Score: 4/10
What Was Stolen
Hackers accessed user database:
- Names and addresses
- Email addresses
- Encrypted passwords
- Phone numbers
- Birth dates
Why It Still Matters
eBay usernames often match other online accounts. The birth dates enable identity verification bypass. Old eBay accounts with purchase history show spending patterns and financial capacity.
27. Adobe (2013) – 153 Million Accounts
Danger Score: 5/10
What Was Stolen
Major breach exposed:
- User IDs and email addresses
- Encrypted passwords
- Password hints (in plaintext)
Why It Still Matters
Password hints were stored unencrypted. Common hints like “first pet” or “mother’s maiden name” answer security questions across multiple platforms. These hints are permanent social engineering fuel.
28. Uber (2016) – 57 Million Users
Danger Score: 6/10
What Was Stolen
Hackers stole driver and rider data:
- Names and email addresses
- Phone numbers
- Driver’s license numbers (for drivers)
- Location history
Why It Still Matters
Uber paid hackers $100,000 to delete the data and cover up the breach for a year. This sets a dangerous precedent. It also means the data may still exist despite the payment. Driver’s licenses enable identity fraud.
29. Dropbox (2012) – 68 Million Users
Danger Score: 4/10
What Was Stolen
Old breach data surfaced years later:
- Email addresses
- Hashed passwords
Why It Still Matters
Dropbox stores documents, photos, and sensitive files. Compromised accounts give attackers access to years of stored data. Many users never changed passwords after the 2012 breach.
30. T-Mobile (2021) – 76 Million People
Danger Score: 8/10
What Was Stolen
One of many T-Mobile breaches:
- Names and addresses
- Social Security Numbers
- Driver’s license information
- Birth dates
Why It Still Matters
T-Mobile has suffered multiple breaches. This shows systemic security failures. SSNs enable identity theft. Driver’s license data enables fake ID creation. T-Mobile customers remain at elevated risk.
31. Sony PlayStation Network (2011) – 77 Million Accounts
Danger Score: 6/10
What Was Stolen
Network outage and breach exposed:
- Names and addresses
- Email addresses
- Birth dates
- Passwords
- Credit card numbers (possibly)
Why It Still Matters
This breach showed gaming networks are high-value targets. Many users were children at the time. Their data remains in criminal databases. Password reuse from gaming accounts affects bank accounts today.
32. Target (2013) – 40 Million Credit Cards
Danger Score: 5/10
What Was Stolen
Point-of-sale malware captured:
- Credit card numbers
- Cardholder names
- Expiration dates
- CVV codes
Why It Still Matters
This breach proved third-party vendors are weak points. Target was hacked through an HVAC contractor’s network access. The cards themselves have expired. But the attack method is now standard.
33. Home Depot (2014) – 56 Million Cards
Danger Score: 5/10
What Was Stolen
Similar point-of-sale attack stole:
- Credit card numbers
- Cardholder data
Why It Still Matters
Like Target, this shows retail infrastructure vulnerabilities. The cards are expired. But the attack blueprint is used in current breaches. Payment systems remain vulnerable to malware.
34. Marriott (Second Breach – 2020) – 5.2 Million Guests
Danger Score: 6/10
What Was Stolen
Using stolen employee credentials:
- Names and contact details
- Loyalty account information
- Additional personal data
Why It Still Matters
Marriott suffered a massive breach in 2018. Then again in 2020. This shows repeat victimization. Companies that get breached once often get breached again. Their security culture is broken.
35. Telegram (2020) – 42 Million Records
Danger Score: 5/10
What Was Stolen
Iranian user data leaked via third-party fork:
- User IDs
- Phone numbers
- Account information
Why It Still Matters
Telegram markets itself as secure and private. This breach proved third-party app versions can be compromised. Iranian activists and dissidents were specifically targeted. Phone numbers enable tracking.
36. Snapchat (2013) – 4.6 Million Users
Danger Score: 4/10
What Was Stolen
API vulnerability exposed:
- Usernames
- Phone numbers
Why It Still Matters
Snapchat users skew young. The leaked phone numbers enabled years of targeted spam toward minors. The small scale makes individual targeting easier.
37. Clubhouse (2021) – 1.3 Million Records
Danger Score: 3/10
What Was Stolen
SQL database leaked for free:
- User IDs
- Real names
- Social media handles
Why It Still Matters
Clubhouse promised exclusivity and privacy. The breach showed social networks scrape data aggressively. Many users were startup founders and investors. The leaked connections reveal business networks.
38. Canva (2019) – 137 Million Users
Danger Score: 4/10
What Was Stolen
Design platform breach exposed:
- Usernames and emails
- Real names and cities
- Hashed passwords (using bcrypt)
Why It Still Matters
Canva stores design work and brand assets. Compromised accounts give competitors access to unreleased marketing materials. The bcrypt hashing is strong. But many users never changed passwords.
39. Zynga (2019) – 218 Million Users
Danger Score: 3/10
What Was Stolen
“Words with Friends” players lost:
- Names and email addresses
- Login credentials
- Facebook IDs (if connected)
Why It Still Matters
Gaming data seems harmless. But email addresses feed spam operations. Facebook IDs enable social engineering. Children’s gaming accounts were included.
40. Under Armour / MyFitnessPal (2018) – 150 Million Users
Danger Score: 5/10
What Was Stolen
Fitness app breach exposed:
- Usernames and emails
- Hashed passwords
Why It Still Matters
Fitness data reveals daily routines and locations. When you run, where you run, when you’re away from home. This enables burglary timing. The data shows health conditions and fitness levels.
41. Chegg (2018) – 40 Million Users
Danger Score: 4/10
What Was Stolen
Education platform leaked:
- Email addresses
- Hashed passwords
- Usernames
Why It Still Matters
Chegg users are students. The emails are often .edu addresses. These enable student discount fraud and academic record access. Many students use the same password for their university accounts.
42. Ashley Madison (2015) – 32 Million Users
Danger Score: 8/10
What Was Stolen
Controversial affair site exposed:
- Real names and addresses
- Email addresses
- Sexual preferences
- Private messages
- Credit card transaction records
Why It Still Matters
This wasn’t just a breach. It was weaponized exposure. Marriages ended. Careers were destroyed. Some victims died by suicide. The site promised discretion. The breach proved digital anonymity is impossible.
43. Cambridge Analytica / Facebook (2018) – 87 Million Users
Danger Score: 7/10
What Was Stolen
Not a breach, but improper data harvesting:
- Facebook profiles
- Friend networks
- Likes and interests
- Private messages
Why It Still Matters
This showed how apps can harvest data from your friends without their consent. The data was used for political profiling and targeting. It proved social networks sell influence, not just ads.
44. Twitch (2021) – 125GB of Data
Danger Score: 6/10
What Was Stolen
Amazon-owned platform leaked:
- Entire source code
- Creator payout reports
- Internal tools and infrastructure
Why It Still Matters
Leaked source code reveals security vulnerabilities hackers can exploit forever. Creator earnings were exposed publicly. This enables targeted financial scams. Streamers now know each other’s income.
45. Microsoft Exchange Server (2021) – 30,000+ Organizations
Danger Score: 9/10
What Was Stolen
State-sponsored attack compromised:
- Corporate email accounts
- Internal communications
- Confidential business data
- Customer information
Why It Still Matters
This wasn’t individual users. It was entire companies. Small businesses, law firms, hospitals. The attackers were state-sponsored (likely China). They installed backdoors. Many companies still don’t know they were compromised.
46. Microsoft Power Apps (2021) – 38 Million Records
Danger Score: 7/10
What Was Stolen
Misconfigured portals exposed:
- Customer data from American Airlines, Ford, and others
- Personal information
- Internal company records
Why It Still Matters
Default settings were insecure. Companies didn’t realize their data was public. This shows cloud platforms require expertise to configure safely. Most small businesses lack this expertise.
47. LinkedIn Password Breach (2012) – 165 Million Users
Danger Score: 5/10
What Was Stolen
Old breach resurfaced years later:
- Email addresses
- Passwords (weakly hashed)
Why It Still Matters
LinkedIn was breached in 2012. The data surfaced for sale in 2016. Many users never changed passwords in that four-year window. Professional emails often match corporate account passwords.
48. Microsoft Customer Support (2019) – 250 Million Records
Danger Score: 6/10
What Was Stolen
Internal database left exposed:
- Customer service records
- Support ticket conversations
- Email addresses
- Case details
Why It Still Matters
Support tickets reveal system problems, software versions, and security questions users ask. This intelligence helps hackers craft better attacks. Microsoft’s response time was slow.
49. Instagram / Facebook Third-Party Apps (2018) – Millions of Users
Danger Score: 6/10
What Was Stolen
Multiple third-party apps stored:
- Instagram passwords in plaintext
- User credentials
- Account access tokens
Why It Still Matters
This wasn’t one breach. It was systemic. Multiple apps were storing passwords insecurely. Users trusted Facebook’s platform. The platform failed to audit third-party security practices.
50. Yahoo (2012) – 1 Billion Accounts
Danger Score: 4/10
What Was Stolen
A second, separate Yahoo breach:
- Names and emails
- Passwords (hashed)
- Security questions
Why It Still Matters
Yes, Yahoo appears twice in this list. They suffered multiple breaches. This one happened in 2012 but wasn’t disclosed until 2016. The delay gave criminals four years of undetected access. Yahoo’s security was broken at every level.
Pattern to Notice: These 30 breaches span 15 years of cybersecurity failures. Some exposed credit cards that have now expired. Others exposed permanent data like SSNs and medical records. The common thread? Companies consistently prioritize growth over security. They collect more data than necessary. They store it longer than needed. Then they fail to protect it. Every breach in this list was preventable.
What Do All These Leaks Have in Common?
You’ve just read about 50 massive data breaches. Billions of records stolen. Trillions of dollars in damage. Millions of lives disrupted.
Here’s what they all share:
They all promised security. Every single company on this list claimed to protect your data. They had privacy policies and had security teams and even had certifications and compliance badges.
They all failed.
Some failed through negligence and Some through outdated systems and some of them through third-party vendors. Some through employees who clicked a phishing link.
But the result is the same. Your data is out there. On criminal forums. In spam databases. Traded between hackers for pennies.
And here’s the uncomfortable truth: More breaches are coming.
The companies holding your data right now will be breached tomorrow. Or next month. Or next year. Not “if.” When.
So what do you do?
You Cannot Trust Corporations to Hold the Wall
The evidence is overwhelming. Big Tech cannot protect you. Banks cannot protect you. Healthcare providers cannot protect you.
You must become your own firewall.
This doesn’t mean paranoia. It means preparation, defense and accepting reality and adapting.
The good news? You can protect yourself. Right now. Today.
Here’s where to start:
Step 1: Find Out If You’re Already Exposed
Before you can defend yourself, you need to know the damage.
Check your exposure status now:
Most people are in multiple breach databases. Some are in dozens. You need to know which ones.
👉 Check If Your Data Was Leaked (Without Getting Scammed)
This free guide walks you through:
- How to safely check breach databases
- How to search your own inbox for breach notifications
- How to use your browser’s built-in password checker
- How to verify if specific breaches affected you
Don’t skip this step. You can’t fix what you don’t know about.
Step 2: Lock Down Your Identity
Once you know your exposure, you need to build defenses.
Password changes aren’t enough. Email changes aren’t enough. You need a complete security overhaul.
Your complete defense strategy:
👉 The Ultimate Guide to Digital Self-Defense
This comprehensive guide covers:
Immediate Actions (Do These Today):
- Freeze your credit with all three bureaus
- Enable two-factor authentication everywhere
- Change passwords for critical accounts
- Set up credit monitoring alerts
Medium-Term Defenses (This Week):
- Use password managers for unique passwords
- Create email aliases for different services
- Review and revoke third-party app permissions
- Set up virtual credit cards for online purchases
Long-Term Strategy (This Month):
- Implement multi-layered security
- Create an identity theft response plan
- Monitor dark web exposure
- Build a secure digital vault for important documents
The guide is free. It’s comprehensive. It’s written in plain English.
Most importantly, it works.
Step 3: Stay Updated
New breaches happen every week. New threats emerge constantly.
You can’t fix everything at once. But you can stay informed.
Subscribe to breach alerts: Get notified when new major breaches happen. Know if your data is involved before criminals start using it.
Follow security news: Major breaches make headlines. Follow trusted security researchers on social media.
Check this page regularly: We update this list as new breaches emerge. Bookmark it. Come back monthly.
The Reality Check
Reading this list is overwhelming. We know.
You’re thinking: “I’m in 20 of these breaches. What’s the point of even trying?”
Here’s the point:
Every layer of defense matters. Criminals target easy victims. They use automated tools. They look for low-hanging fruit.
When you freeze your credit, you’re not in the “easy” category anymore and after that you use unique passwords, credential stuffing attacks fail and then you use two-factor authentication, stolen passwords become worthless.
You won’t be 100% safe. Nobody is. But you’ll be safer than 95% of people.
And that’s usually enough.
Take Action Now
You have three choices:
Option 1: Do Nothing – Hope you won’t be the victim of identity theft, tax fraud, or account takeover. Hope criminals choose someone else.
Option 2: Panic – Feel overwhelmed. Close this tab. Pretend the problem doesn’t exist. Wait until something bad happens.
Option 3: Take Control – Spend 30 minutes today building defenses. Spend 30 minutes next week improving them. Gradually become a harder target.
We’ve given you the roadmap. The tools are free. The information is here.
All you need to do is start.
👉 Step 1: Check Your Exposure Status
👉 Step 2: Build Your Defenses
Final Thought
Data breaches will never stop. New companies will fail and vulnerabilities will emerge an then new hackers will appear.
But you don’t have to be an easy victim.
You don’t have to wait for the next company to fail you.
You don’t have to trust corporations to protect what they’ve proven they cannot protect.
Yes You can take control. Today.
The 50 breaches on this list affected billions of people. Most did nothing. They stayed exposed. They stayed vulnerable.
Don’t be most people.
Last Updated: January 2026
This page is regularly updated as new breaches emerge. Bookmark it and check back monthly.
Have feedback or found an error? Use the thumbs down button below to let us know. We read every submission.
Pingback: The Pixel Defence Protocol: How to Bulletproof Your Identity in 2026
Pingback: Equifax Data Breach: The "Forever Leak" & Why You Must Freeze Your Credit (2026 Guide) - Pixel Defence